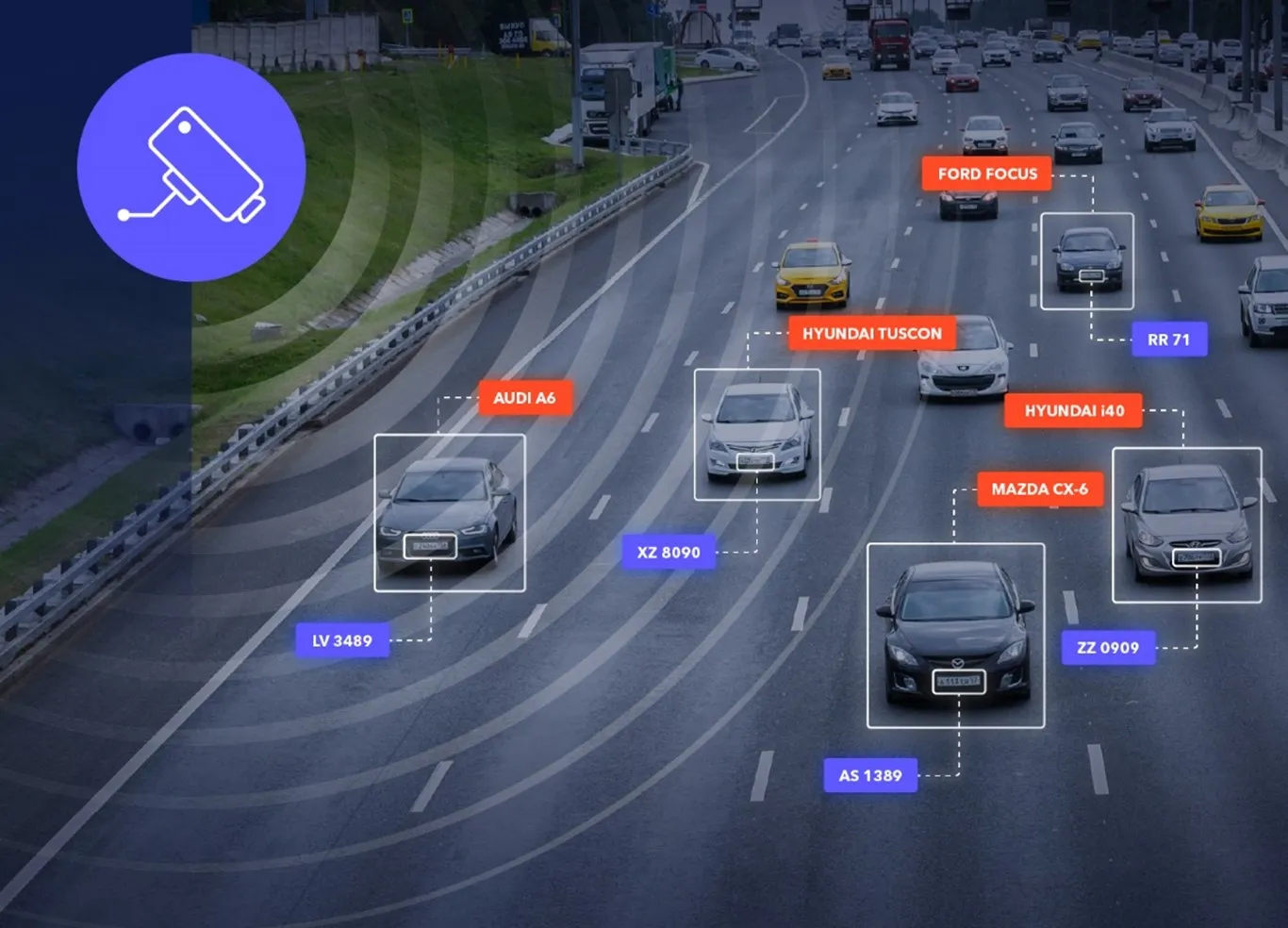
Surveillance camera technology has come a long way over the last 20 years as visitors to the Axis Communications booth here at ITS America 2016 San Jose will see. The company invented the network camera in 1996, making it possible to connect a video camera directly to a computer network (commonly referred to as IP video). The shift from analog to IP has changed the global security market. According to Axis, with network cameras being based on open IP standards, authorised users can get secure and flexible a
June 14, 2016
Read time: 2 mins

Surveillance camera technology has come a long way over the last 20 years as visitors to the 2215 Axis Communications booth here at ITS America 2016 San Jose will see. The company invented the network camera in 1996, making it possible to connect a video camera directly to a computer network (commonly referred to as IP video). The shift from analog to IP has changed the global security market. According to Axis, with network cameras being based on open IP standards, authorised users can get secure and flexible access to their video and analytics via a computer or mobile device from anywhere - resulting in increased efficiency. And unlike its anaog predecessor, IP video provides superior image usability in challenging low- and back-light conditions, camera intelligence and open standards.
Here in San Jose, Axis is demonstrating its latest innovations in IP video technology by showcasing cameras with zoom capabilities and discussing new technologies such as wide dynamic range – forensic capture, electronic image stabilisation, and Axis’ zipstream technology - a technology that reduces bandwidth and storage without sacrificing image quality. “It is these types of intelligent camera capabilities that make it possible to alert traffic management centres and other users automatically when there is an incident, enabling faster redirection of traffic and dispatch of emergency services,” says Anthony Incorvati, business development manager at Axis Communications. “These types of analytics are also being used to collect important data to support planners and engineers for future projects.”
Here in San Jose, Axis is demonstrating its latest innovations in IP video technology by showcasing cameras with zoom capabilities and discussing new technologies such as wide dynamic range – forensic capture, electronic image stabilisation, and Axis’ zipstream technology - a technology that reduces bandwidth and storage without sacrificing image quality. “It is these types of intelligent camera capabilities that make it possible to alert traffic management centres and other users automatically when there is an incident, enabling faster redirection of traffic and dispatch of emergency services,” says Anthony Incorvati, business development manager at Axis Communications. “These types of analytics are also being used to collect important data to support planners and engineers for future projects.”